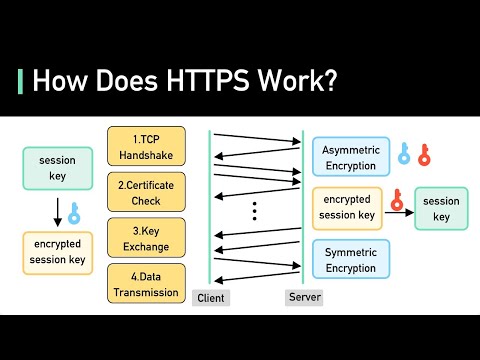
Securing FTP over SSL [Windows Server 2019] I (tobor), cover how to secure the configuration and directory permissions for a Windows Server 2019 FTP over SSL server using IIS. If you like what you see please Subscribe! 0:00 Intro Summary 0:53 Active Directory Users and Groups 1:37 Covering how the contents of the file is used with 2:30 FTP Directory locations (Network Share or Local Folder) 3:00 Adding users in CSV file to Admin or Users group in AD 3:38 Install Script for FTPS Server 4:10 Started Script Execution 4:50 Begin entering prompted values for AD Users and the permissions you want assigned 5:43 Name the IIS Manager FTP Site 5:53 Define the home directory for the FTP site 6:11 Explicit SSL or Implicit SSL connections 6:25 Difference between Explicit and Implicit connections 7:41 Firewall rule created for defined port 7:58 FTP Root directory folder was created and IIS Site created 8:22 Create Local FTP User group 8:35 Create a Local FTP user 9:12 Authorization Rules added to FTP Site 9:35 Basic Authentication enabled 9:53 Set permissions on the created folder for the FTP service 10:20 View permissionson FTP sites root directory 10:35 AD Attribute values getting pulled by FTP Service 11:39 Assigning an SSL certificate to the FTP Service 12:00 How the script auto discovers an SSL certificate using FriendlyName value 12:50 Define Passive Ports 13:14 How to Re-Define Passive ports in IIS Manager if desired 13:53 IP address required for clients on the other side of a router or firewall 14:16 How an IP Address is automatically determined with DHCP 14:40 Virtual Host name for the FTP site in IIS Manager Bindings 15:10 The hosts file on windows to add vhost names too 15:51 Firewall rule created for Passive FTP Ports defined earlier 16:06 128 bit encryption enabled 16:14 FTP Site restarted and port is confirmed open 16:30 FTP SSL Settings 16:57 Custom FTP Messages and Max Connections 17:27 Restict FTP Access based on IP address of clients 17:55 User Isolation values obtained from AD 18:08 Network Share Directory Permissions 18:33 Using FileZilla to access the FTPES or FTPS Instance 19:06 Sign into FTPES Server using an FTP-Admins member 19:28 Upload files with FTP-Admins user 19:41 Download file with FTP-Admins user 19:57 Make AD values for the FTP-Admins user so FTP Home directory is inaccessible 20:42 Sign into FTPES server with FTP-Users member (entered incorrect password on first attempt) 21:19 View AD Attributes of the FTP-Users member 21:34 View permissions on the network share permission for the FTP-Users member 22:09 Download files using FTP-Users member 22:18 Upload files denied because of FTP-Users group permissions 22:36 Add FTP-Users member to the local FTPUsers group to add Read,Write permissions 23:04 Add Write permissions to the local FTPUsers group 23:34 Connect to FTPES server with new permissions (Restart of FTP service required) 24:12 FTPUsers group successfully uploaded files 24:41 More restrictive permissions dont get applied 25:13 FTPES sign in using FTPUsers member accessing a local directory instead of a network share 26:07 AD Attributes assigned to ftpsuser accessing local FTP directory 26:48 Sign in to FTPES using an FTP-Users member with Read permissions only (Remove AD FTP-Users group from FTPUsers group) 27:58 Verify local group membership and verify upload was denied 28:43 Outro View my Verified Certifications! Follow us on GitHub! Official Site Give Respect on HackTheBox! Like us on Facebook! View PS Gallery Modules! The . Security Package
- 5184Просмотров
- 4 года назадОпубликованоOsbornePro TV
Securing FTP over SSL [Windows Server 2019]
Похожее видео
Популярное
Бобр добр
Wb effects not scary
Городской снайпер 3
малыш вилли
oso
Городской снайпер 1 серия
forsaken fandom
Xspb by kirk
Big cats size comparison
Universal mirror g major
РОЖДЕСТВО С КАЮ
Грань провосудия 4серия
Classic caliou misbehaves on a road trip Rosie
Teletubbies
маленькая девочка
реклама для детей
Pussy
Утопая в любви
улица далматинцев 101
klaskyklaskyklasskyklasky joey 2 do go
ПЕРСИ И ДРУЗЬЯ
jewish girls
historia com slime menina dançando funk
Пим и пэм
Wb effects not scary
Городской снайпер 3
малыш вилли
oso
Городской снайпер 1 серия
forsaken fandom
Xspb by kirk
Big cats size comparison
Universal mirror g major
РОЖДЕСТВО С КАЮ
Грань провосудия 4серия
Classic caliou misbehaves on a road trip Rosie
Teletubbies
маленькая девочка
реклама для детей
Pussy
Утопая в любви
улица далматинцев 101
klaskyklaskyklasskyklasky joey 2 do go
ПЕРСИ И ДРУЗЬЯ
jewish girls
historia com slime menina dançando funk
Пим и пэм
Новини